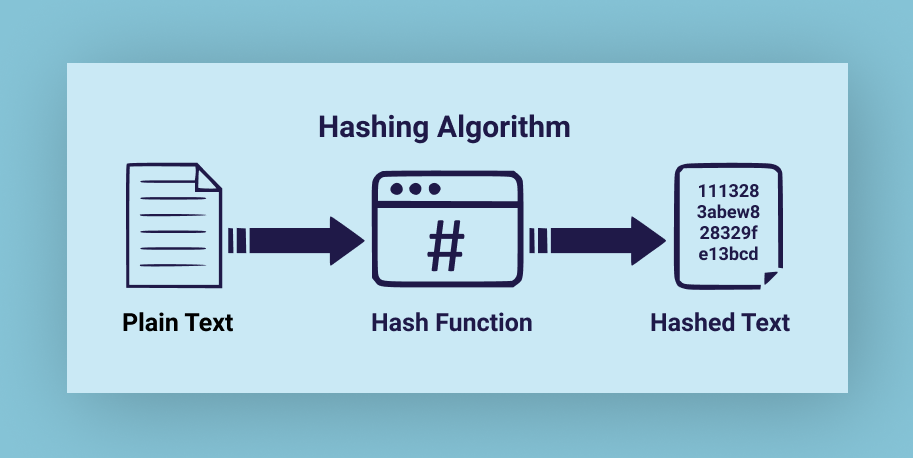
As the madness of the digital world is taking over our lives, where sharing critical information and data has become a common phenomenon, data security has become the most discussed topic more than ever. Cryptographic hashing has long been a crucial component of cybersecurity and data security.
In reality, it is a common component of many technologies, including the protocols for Bitcoin and other cryptocurrencies. The inventor of hashing is Hans Peter Luhn, a prominent scientist at IBM. Hashing and its application have come a long way since then. This article discusses in detail the use of hashing in cryptography.
What does hashing mean in cryptography?
Hashing is a mathematical algorithm that transforms any given key or string of characters of any length into an encrypted output of a specific length. Therefore, its unique hash will always be the same size regardless of the original quantity of data or file size involved.
A hash function works as a one-way function; you can enter data to produce a unique string using a hashing algorithm, but if anyone discovers a new hash, they are unlikely to figure out what was the original data.
Implementing hash tables is the most well-liked implementation of hashing. All value pairs are kept in the hash table’s list, which can be accessed quickly using its index. The end result is a way of efficiently obtaining essential values in a database table while enhancing a database’s security through encryption.
A hash value, also known as a digest, is the result of the hash operation. Use of hashing in cryptography mainly contributes to confirming the validity of data. Passwords frequently make use of hash functions. Any secure database that stores passwords stores them as digests or hash values.
Properties of hash function in cryptography are as follows:
- A hash algorithm should be deterministic, which means that regardless of the size of the initial input, it always produces an output of the same size.
- It is impossible to reverse a hash value and obtain the original input plaintext message. Thus, the idea is that hashes are one-way, irreversible processes.
- A hash value is collision resistance. That means It ought to be impossible to find two different passwords that hash to the same ciphertext.
- Diffusion or Avalanche effect. It means that every alteration to the input, no matter how small, will cause a significant alteration to the output.
- A hash algorithm should operate at a fairly reasonable speed and compute hash values quickly. It is an ideal characteristic of a cryptographic hash function.
- Compression is another property of cryptographic hashing. The hash function output is substantially smaller than the size of the input.
Why is hashing used?
In order to transmit transaction information anonymously, cryptographic hash functions help cryptocurrencies tremendously. For instance, the algorithm of Bitcoin, the first cryptocurrency, uses SHA-256 Crypto hashing. However, it has other real-world applications. Some of these applications are as follows:
Data retrieval
Utilizing algorithms or functions, hashing converts object data into a practical integer value. The search for these objects on that object data map can then be narrowed using a hash. For instance, developers store data in the form of key and value pairs in hash tables. The hash code is then translated to a fixed size, and the key serves as an input to the hashing method to help identify the contents.
Password protection
Many organizations employ hashing algorithms to secure customer login information on their systems. It provides an additional layer of security. It ensures that even if hackers enter the organization’s servers, they cannot access or interpret the data inside.
File Integrity
Hashing also aids in maintaining the integrity of files. Verifying that a downloaded file is legitimate and free of malware is crucial, given the rise in internet threats. Websites provide users with the file’s hashed value so they can check the file’s integrity.
Digital Signature
Hashing helps to encrypt and decrypt digital signatures that authenticate message senders and recipients. In this case, the hash function alters the digital signature before transmitting the hashed value and the signature to the recipient. When a message is received, the same hash function uses the signature to create the message digest, which is then compared to the transmitted one to ensure they are identical.
It is important to note that Hashtools is a user-friendly software tool that simplifies and speeds up computation for CRC32, MD5, SHA1, SHA256, SHA384, and SHA512 hashes. It is beneficial for all users to validate the integrity of files by comparing them to these signatures and to determine whether or not two files have the same content.
What is hashing for security?
Utilizing a unique cryptographic procedure, hashing converts one piece of data into another of a fixed length. A hash table converts the data of arbitrary size to a set length, and the resultant data is then stored in the digest. In the context of security, even if the hash function is known, it is practically impossible to reconstruct the input data from the output.
For example, every time someone creates an account that needs a password, the password is hashed and then stored in the digest. When that person enters the password again during the subsequent login attempt, the digest will be compared to the prior one to ensure an exact match.
It’s important to note that even if a database is compromised, the attacker cannot access sensitive information right away because there is no simple way to locate the information that resulted in the hash they now hold.
What are the 3 types of hashing?
Types of hashing in cryptography have grown in number over the years. Each of them has different functions and uses. Developers, firms, and cyber security specialists prefer one over the other due to their distinct natures. But each of them serves the same purpose– security and integrity. Hash function in cryptography example are as follows:
MD-5
It was designed in 1991 and was one of the first hashing algorithms to gain popularity.
It transforms a string into a 128-bit fingerprint. A function known as checksum verifies its data integrity. However, the MD-5 hash suffers from severe hash collisions because of its age, losing its popularity among data security experts.
SHA (Secure Hashing Algorithm)
The US Government developed the initial version of Sha cryptography hashing. Compared to the MD-5 method, they are more secure and more difficult to crack. The SHA algorithm is available in many variations. Six hash functions having hash values of 224, 256, 384, or 512 bits are included in the SHA-2 algorithm and were developed by the National Security Agency (NSA).
CR32
A cyclic redundancy check (CRC), which can identify unintentional data changes, is the basis of the CRC32 hashing technique. Data encoding using CR32 protocol always produces a hash output of fixed length. The CRC32 method is used by servers that support zip files and file transfer protocol (FTP).
Why is hashing important in cyber security?
Since its inception in 1941, hashing algorithms have advanced significantly, and because of their distinctive qualities, they are now an integral part of cybersecurity. Over time the world of cybersecurity has seen the need for hashing in its various aspects.
Hashing is used in several encryption algorithms to improve cybersecurity. Without a decryption key, hashed text and inputs are useless to hackers. For instance, if hackers infiltrate a database and discover critical information like “Constantine, Credit Card No. 123456,” they cannot exploit that data for malicious purposes.
However, the same information produces a fixed hash value when it is hashed, such as “b33456k7,” rendering it worthless for bad actors unless they possess the necessary decryption keys.
There are numerous uses for hashing in cybersecurity. The most typical ones include blockchain, password validation, file integrity, and message integrity. Each of these use cases has one fundamental purpose of hashing, which is to safeguard against tampering with data or files.
What is the most secure hashing method?
With the advancement in technology, hashing algorithms have gone through a significant change. Although there are various hash methods, SHA remains the most secure hashing method to date. Here is a deeper insight into the most secure hashing method.
NIIST developed the SHA (Secure Hash Algorithm) series of algorithms. Due to the avalanche effect, even a slight modification to the data that needs to be encrypted could produce a drastically different hash string.
The SHA algorithms are thought to provide a decent randomization function because they exhibit avalanche effect symptoms. The MD4 and MD5 algorithms created by Ron Rivest served as the foundation for SHA algorithms. The national security agency published SHA as a US government standard.
The initial version of the secure hashing algorithm was SHA-0. It was pulled out shortly after its release due to its flaws. In 1994 it made a reappearance as SHA-1 after fixing previous issues. However, Xiaoyun Wang, a well-known Chinese cryptographer, successfully cracked the common hashes, demonstrating that SHA-1 is not as secure as it formerly was.
The SHA-1 algorithm serves as the foundation for SHA-2. The SHA-224, SHA-256, SHA-384, and SHA-512 algorithms combine into the SHA-2 hash function. The most secure hashing method to this day is still SHA-256. Many software companies and institutions, including the US government, utilize it to safeguard sensitive data, and it has never been reverse-engineered.
Conclusion
This marks the completion of the comprehension of the use of hashing in cryptography. Hashing has many applications, including cryptocurrencies, password protection, signature verification, and other areas. Long used in cybersecurity, cryptographic hashing is now poised to fuel and safeguard the next wave of blockchain applications.