MPC-powered, Zero Trust Inheritance Vault for
Seed Phrases
Passwords
NFTs
Art work
all digital assets
Secure your spot to qualify for 1-year access.
Quantum and hacker-resistant vault for self-custody owners.
Demand Unbeatable Security
Multi-party computation (MPC) technology
Shamir’s Secrets Algorithm
Elliptic-curve Diffie-Hellman (ECDH) algorithm
AES 256 Encryption
AI powered Biometric ID Validation
Leave a legacy and protect your family’s future.
$250 million in crypto was lost along
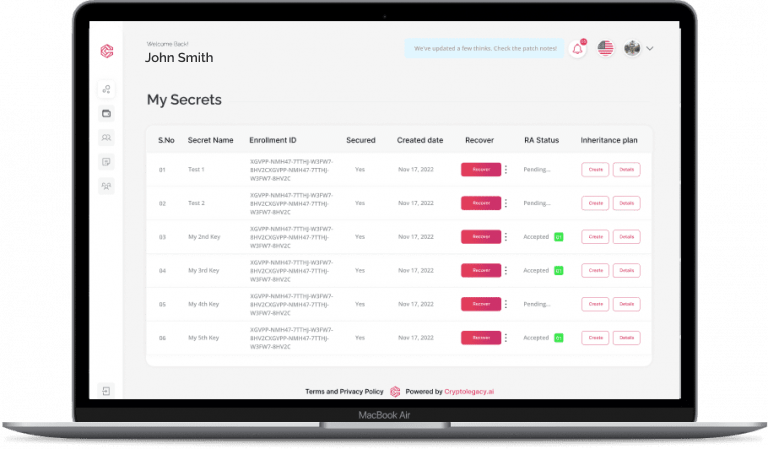
Provide an Effective Inheritance Plan
Inheritance Planning Made Infinitely Easier
How it works
-
Setting up the account
Set up your account and appoint a minimum of 3 loved ones as Recovery Agents (RAs). -
Configure your MPC Quorum
After a minimum of three Recovery Agents have accepted the request, set the minimum quorum and finalise the Agents. -
Enrolling secrets
Once MPC configuration is completed, enroll the secrets. -
Set up Inheritance
You can set up an inheritance for each of your vaults. A simple 5-step workflow enables you to designate your trusses, beneficiaries and asset distribution for the vault.
Most advanced vault on the planet.
Lokblok team’s achievements:
- Engineered the first hardware security modules (HSMs) certified for FIPS 140
- Developed the first HSMs for split keys certified and used by Visa and MasterCard
- First to license RSA patents in the USA to create HSMs in smart cards and USB devices
- Selected by Microsoft to create the first Windows crypto service provider for AES and Elliptic Curve Cryptography with HSMs
- Developed and licensed the first message security protocol for secure email using HSMs to Microsoft
- Developed the first HSMs for split keys certified and used by Visa and MasterCard
- Developed the first security platform to protect the western power grid
- First to create a secure tablet to protect SECRET data for Government
Best-in-class AI Powered ID Validation
They love it, you will too!
Javier Vicente Gonzalez
Casper Labs
“ The CryptoLegacy project is solving one of the most recurrent and important current real problems but focused on the digital assets, crypto /nfts. First they are solving the fact that the users can recover their accounts avoiding losing all their assets. Second, for the present/future they are making sure that these assets automatically are transferred to
the recipients already stated in their smart contracts. This is really important because otherwise these assets will be frozen or lost. ”

James Burns
Estate Attorney
“The most significant thing we can do for the future is provide the tools for the digital landscape that consolidates it all for those we leave behind. The future is now with Cloud Locker in my mind and once the public catches on how it work, I’m sure it will become a planning staple.” 
Travisse Hansen
Co-Founder Radiant Wallet
“Crypto Legacy fills a gaping hole in Defi ecosystem. If Defi is going to
eventually surpass Tradfi then inheritance and estate planning have to
be solved - people just won’t move there money here otherwise.
CryptoLegacy saw that coming and made it surprisingly easy regardless
of which exchange or wallet you use." 
Learn From Fellow Experts
Commonly Asked Questions
MPC (Multi-party Computation) secret sharing is a technique that divides a secret input into shares and distributes them among multiple parties (we call them as Recovery Agents). This method is used to protect the input’s privacy and security. Shamir’s secret sharing is a common method used for this purpose. Here, the input is divided into n shares (equal to the number of Recovery Agents), and the owner sets a minimum threshold of shares required to reconstruct the original input.Each share is then given to the Recovery Agent, ensuring that no one party has access to the entire input. When the original input needs to be reconstructed, the shares are combined using polynomial interpolation. At least the minimum threshold of shares is required to reconstruct the original input.
In MPC secret sharing, the owner of the secret divides the input into encrypted shards and distributes them among the Recovery Agents. The owner can then request the shards from the agents, uses cryptographic algorithm to combine them to reconstruct the original input when needed.
In summary, MPC secret sharing allows the owner to divide their input into shards, distribute them among the Recovery Agents, and reconstruct the original input by combining the shards using a cryptographic algorithm.
At Crypto Legacy, we apply additional layers of process to protect and safeguard secrets. To learn more about how we use MPC for secret protection, please visit our website.
According to an NBC poll, a fifth of all Americans has used crypto and there are over eighty million crypto wallets worldwide. With so many people invested in crypto, it is extremely important to understand how to protect the keys to use these wallets. It is reported that there have been over one hundred high-volume hacks worldwide to date that affect almost all crypto investors. The problem of protecting wallets is so important that the US Federal Government issued a warning letter to the banks in January 2023 advising them about the risks of hacks,
Joint Statement on Crypto-Asset Risks to Banking Organizations (fdic.gov).
It is a fact that crypto is both difficult and cumbersome to store securely! People often leave their wallet keys in the cloud, where it becomes a huge collective target for hackers, or as a picture stored on their computer, or printed on paper and put away. If the Secret is stored in the cloud, you have given access to the Cloud Service Provider who has the keys as well as a trove on online hackers. And if a person is safeguarding it themselves, people are careless and can accidentally lose it or have devices that store it fail.
Lokblok is the security partner providing the patent-pending provably secure key management service to the Crypto Legacy offerings. The Lokblok Team has worked together for over 20 years solving difficult problems to protect keys, digital assets, data at rest, and data in transit for Government, financial, and enterprise customers.
No! Secrets Vault is a non-custodial service and we do not store the seed phrase or any part of the Secret anywhere in the system in any form.
Lokblok’s key management system for Secrets Vault is a non-custodial service that combines the power of proven cryptographic algorithms, protocols, and standards that include Shamir’s Secret Sharing algorithm, Multi-party Computation, AES-256, public key cryptography, Elliptic Curve Diffie Helman (ECDH), to create a revolutionary way to backup and restore Secrets and Keys.
The service also uses remote attestation and KYC and/or LiveID to verify and validate asset owners and Recovery Agents.